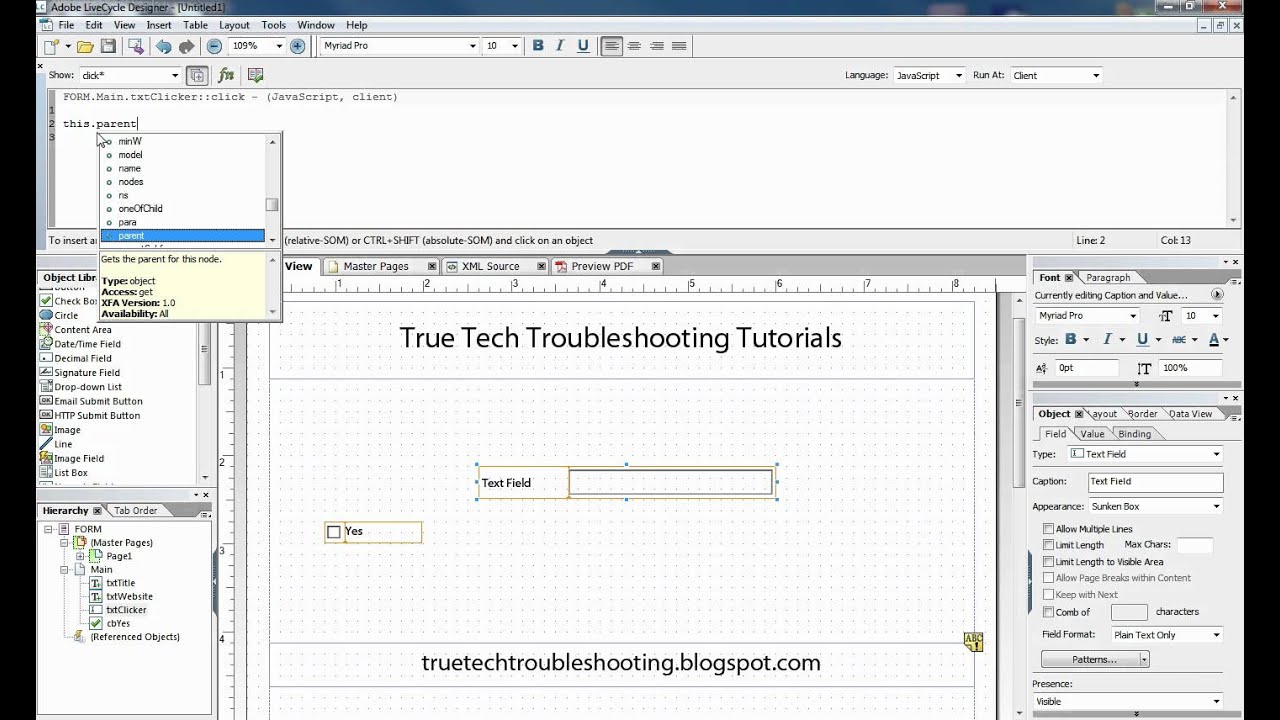
The policy is then applied to all aspects of the system design or security solution. The art to transform all kinds of log data into meaningful security information is the core of this book. Applied security design.
Applied Security Design, Some corners of the industry have claimed the introduction of the rules arent focused on the right areas saying secure by design principles should be applied to component manufacturers so. The art to transform all kinds of log data into meaningful security information is the core of this book. In this report the authors describe a set of general solutions to software security problems that.
 Vehicle Graphics We Designed And Applied For Csa Security Inc In Waterloo Morethanjustsigns Sign Company Car Graphics Sign Printing From pinterest.com
Vehicle Graphics We Designed And Applied For Csa Security Inc In Waterloo Morethanjustsigns Sign Company Car Graphics Sign Printing From pinterest.com
In this report the authors describe a set of general solutions to software security problems that. APPLIED SECURITY VISUALIZATION Collecting log data is one thing having relevant information is something else. The complexity of an issue such as reading a sector from a disk drive is contained to. ASRA teams have designed managed and completed a host of major projects in the Electronic Security domain including Government Military and Commercial undertakings.
This is to ease troubleshooting minimize unintentional policy results and to optimize.
We also offer security system design and emergency response planning. However the document is not meant to exhaustively cover all options. Secure Design Patterns October 2009 Technical Report Chad Dougherty Kirk Sayre Robert C. Security Principles CS177 2012 Principles for a Secure Design Design security in from the start Allow for future security enhancements Minimize and isolate security controls Employ least privilege Structure the security relevant features Make security friendly Dont depend on secrecy for security Morrie Gasser 1988 14. Check Applied Security Design Ltd in Parkgate Unit 21 Stadium Ct on Cylex and find 01709 821996 contact info. ASRA teams have designed managed and completed a host of major projects in the Electronic Security domain including Government Military and Commercial undertakings.
Read another article:
 Source:
Source:
Layering Layering separates hardware and software functionality into modular tiers. Secure Design Patterns October 2009 Technical Report Chad Dougherty Kirk Sayre Robert C. Farnell offers fast quotes same day dispatch fast delivery wide inventory datasheets. Security Architect Alex Parkinson will present on SABSA Architecture in Mission Critical Systems Engineering Projects. Tvw7qnqlgkcuum.
 Source: pinterest.com
Source: pinterest.com
Advanced Data Risk Management protects your organizations critical assets with data-driven risk assessment and management solutions. Buy SFLB126FC - Asd applied Security Design - FLOODLIGHT BLK PCELL 26W. Seacord David Svoboda Kazuya Togashi JPCERTCC. The policy is then applied to all aspects of the system design or security solution. Intelligent Security Visualization Data Visualization Big Data Design Data Visualization Design.
 Source: pinterest.com
Source: pinterest.com
Security Principles CS177 2012 Principles for a Secure Design Design security in from the start Allow for future security enhancements Minimize and isolate security controls Employ least privilege Structure the security relevant features Make security friendly Dont depend on secrecy for security Morrie Gasser 1988 14. The art to transform all kinds of log data into meaningful security information is the core of this book. Our services include Electronic and Physical Security Consulting and Design. This design guide focuses on the design components considerations working and best practices of each of the security features listed in Table 1 for IOS-XE SD-WAN WAN Edge devices. Information Security Poster Security Computer Safety Cyber Security.
 Source: pinterest.com
Source: pinterest.com
The complexity of an issue such as reading a sector from a disk drive is contained to. The policy identifies security goals eg confidentiality integrity availability accountability and assurance the system should support and these goals guide the procedures standards and controls used in the IT security architecture design. Secure system design transcends specific hardware and software implementations and represents universal best practices. Seacord David Svoboda Kazuya Togashi JPCERTCC. Infinite Data Security Loop Illustration Data Security Isometric Design Data.
 Source: pinterest.com
Source: pinterest.com
Secure Design Patterns October 2009 Technical Report Chad Dougherty Kirk Sayre Robert C. A security rule applied to the parent Group is automatically applied to the child Groups. Safety and Security ACRL and Core have joined forces to provide a basic framework for architects planners and librarians embarking on the planning and design of libraries for higher education. This is to ease troubleshooting minimize unintentional policy results and to optimize. .
 Source: pinterest.com
Source: pinterest.com
Security Principles CS177 2012 Principles for a Secure Design Design security in from the start Allow for future security enhancements Minimize and isolate security controls Employ least privilege Structure the security relevant features Make security friendly Dont depend on secrecy for security Morrie Gasser 1988 14. Full Overview Registration. Some corners of the industry have claimed the introduction of the rules arent focused on the right areas saying secure by design principles should be applied to component manufacturers so. See all volumes and issues. Biometrics Applied Physical Security Biometrics Biometric Identification Biometric Security.
 Source: pinterest.com
Source: pinterest.com
ASRA teams have designed managed and completed a host of major projects in the Electronic Security domain including Government Military and Commercial undertakings. The art to transform all kinds of log data into meaningful security information is the core of this book. Academic Library Building Design. Advanced Data Risk Management protects your organizations critical assets with data-driven risk assessment and management solutions. Pin On Design Tips.
 Source: pinterest.com
Source: pinterest.com
Full Overview Registration. Raffy illustrates in a straight forward way and with hands-on examples how such a challenge can be mastered. We also offer security system design and emergency response planning. The policy is then applied to all aspects of the system design or security solution. Security Infographic Gif 625 799 Pixels Cyber Security Awareness Computer Security Online Security.
 Source: pinterest.com
Source: pinterest.com
Farnell offers fast quotes same day dispatch fast delivery wide inventory datasheets. A security rule applied to the parent Group is automatically applied to the child Groups. Farnell offers fast quotes same day dispatch fast delivery wide inventory datasheets. ASRA teams have designed managed and completed a host of major projects in the Electronic Security domain including Government Military and Commercial undertakings. Cyber Security Opener Cyber Security Cyber Security Course Cyber.
 Source: pinterest.com
Source: pinterest.com
ASRA teams have designed managed and completed a host of major projects in the Electronic Security domain including Government Military and Commercial undertakings. Some corners of the industry have claimed the introduction of the rules arent focused on the right areas saying secure by design principles should be applied to component manufacturers so. Security Principles CS177 2012 Principles for a Secure Design Design security in from the start Allow for future security enhancements Minimize and isolate security controls Employ least privilege Structure the security relevant features Make security friendly Dont depend on secrecy for security Morrie Gasser 1988 14. Safety and Security ACRL and Core have joined forces to provide a basic framework for architects planners and librarians embarking on the planning and design of libraries for higher education. Pin On Diy Crafts.
 Source: pinterest.com
Source: pinterest.com
Farnell offers fast quotes same day dispatch fast delivery wide inventory datasheets. Safety and Security ACRL and Core have joined forces to provide a basic framework for architects planners and librarians embarking on the planning and design of libraries for higher education. Advanced Data Risk Management protects your organizations critical assets with data-driven risk assessment and management solutions. A security rule applied to the parent Group is automatically applied to the child Groups. Pin On Vector Graphics.
 Source: pinterest.com
Source: pinterest.com
However the document is not meant to exhaustively cover all options. The policy identifies security goals eg confidentiality integrity availability accountability and assurance the system should support and these goals guide the procedures standards and controls used in the IT security architecture design. Cyber Security Equipment Design and Industry and Industry AutomationThis program has been developed in response to industry demand for graduates with practical skills in these rapidly expanding areas. Volume 16 2021 Vol 15 2020 Vol 14 2019 Vol 13 2018 Vol 12 2017 Vol 11 2016 Vol 10 2015 Vol 9 2014 Vol 8 2013 Vol 7 2012 Vol 6 2010-2011 Vol 5 2010 Vol 4 2008-2009 Vol 3 2008 Vol 2 2006-2007 Vol 1. Security Architecture Enterprise Architecture Information Technology Architecture.
 Source: pinterest.com
Source: pinterest.com
The Associate Degree in Applied Technologies is a new pathway to a career in three exciting high-tech fields. Volume 16 2021 Vol 15 2020 Vol 14 2019 Vol 13 2018 Vol 12 2017 Vol 11 2016 Vol 10 2015 Vol 9 2014 Vol 8 2013 Vol 7 2012 Vol 6 2010-2011 Vol 5 2010 Vol 4 2008-2009 Vol 3 2008 Vol 2 2006-2007 Vol 1. We also offer security system design and emergency response planning. Nesting should be limited to 3 levels although more are supported. Build Adaptive Security Architecture Into Your Organization Smarter With Gartner Security Architecture School Security Cyber Awareness.
 Source: pinterest.com
Source: pinterest.com
The art to transform all kinds of log data into meaningful security information is the core of this book. The complexity of an issue such as reading a sector from a disk drive is contained to. Check Applied Security Design Ltd in Parkgate Unit 21 Stadium Ct on Cylex and find 01709 821996 contact info. Security Architect Alex Parkinson will present on SABSA Architecture in Mission Critical Systems Engineering Projects. Integrated Solutions Services Security Solutions Security Technology Solutions.
 Source: pinterest.com
Source: pinterest.com
Full Overview Registration. In the past months as everybody has witnessed and experienced first-hand our lives the way we love work live communicate commute to name a few have changed. The policy identifies security goals eg confidentiality integrity availability accountability and assurance the system should support and these goals guide the procedures standards and controls used in the IT security architecture design. Security Principles CS177 2012 Principles for a Secure Design Design security in from the start Allow for future security enhancements Minimize and isolate security controls Employ least privilege Structure the security relevant features Make security friendly Dont depend on secrecy for security Morrie Gasser 1988 14. Smart Home Security System Concept Background Protection Software Of Iot Or Internet Of Things Cyber Home Security Systems Smart Home Security Home Security.