It should be dynamic enough to includes various types of audit log under an use case under discussion. The design from the base table to the audit table are very similar but the audit table has some additional columns to support managing the historical data ie. Audit log design pattern.
Audit Log Design Pattern, A common example is logging a SQL command after the execution. These event objects are then processed to cause changes to the system and stored to provide an Audit Log. The auditing code is intertwined with the business logic which makes the business logic more complicated.
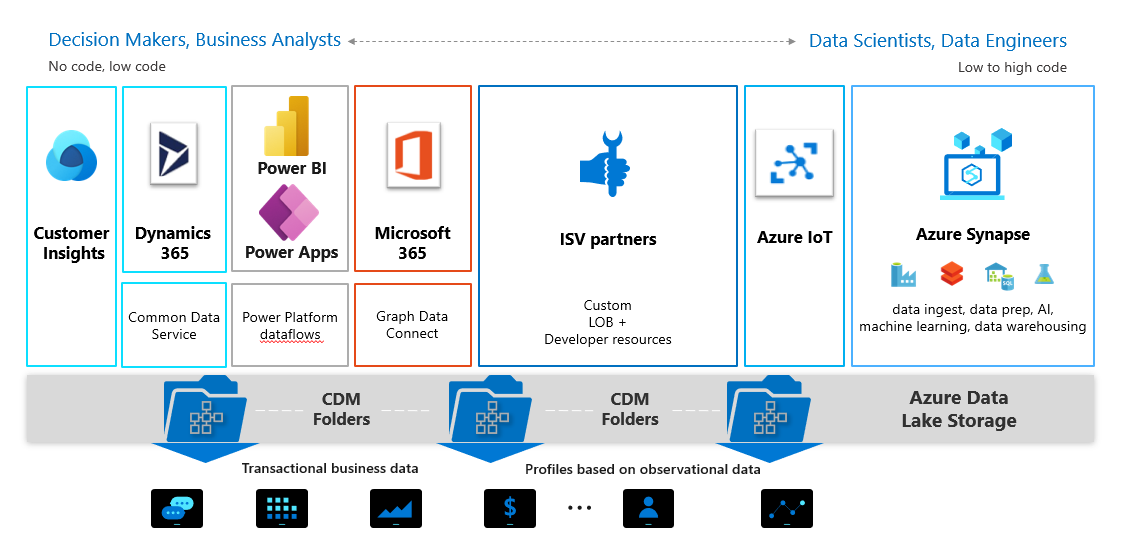 Common Data Model And Azure Data Lake Storage Gen2 Common Data Model Microsoft Docs From docs.microsoft.com
Common Data Model And Azure Data Lake Storage Gen2 Common Data Model Microsoft Docs From docs.microsoft.com
Stores a unique post ID the title content and a deleted flag. Event Sourcing is a reliable way to implement auditing. Theres an audit log thing that collects a bunch of audit record things. Fowler provides an introduction here.
The architectural model upon which this design pattern is based is further covered in.
Any IOC Dependency Injection framework to inject the abstract factory to. Implement DB triggers to capture any change in data states and log in audit tables. Events funnel inputs into a single source. Db contains database and entity framework related codes. Run an audit log search. Here we have a system with inputs from a user interface messaging system and some direct manipulation of database tables.
Read another article:
 Source: dribbble.com
Source: dribbble.com
Audit logging after the action. The design from the base table to the audit table are very similar but the audit table has some additional columns to support managing the historical data ie. Remember that you can use Audit Log in some parts of the model and other patterns elsewhere. This pattern has the following drawbacks. Audit Log Designs Themes Templates And Downloadable Graphic Elements On Dribbble.
 Source: ibm.com
Source: ibm.com
Two tables are required. Custom application level or domain entity id who acts as the performer of the action. In order to manage the growth of involved topics the retention policy for each topic should be well-defined. The architectural model upon which this design pattern is based is further covered in. What Is Data Modeling Ibm.
 Source: docs.microsoft.com
Source: docs.microsoft.com
In case of an exception the log entry might not be written so the audit log will not provide relevant contextual information for the exception. AuditID to serve as the identity ModifiedBy to serve. So you might handle actual time history of a property with Temporal Property and use Audit Log to handle the. The Admin Activity and Data Access audit logs are both exported in this format. Common Data Model And Azure Data Lake Storage Gen2 Common Data Model Microsoft Docs.
 Source: aws.amazon.com
Source: aws.amazon.com
This pattern has the following benefits. It should be dynamic enough to includes various types of audit log under an use case under discussion. These design patterns are useful for building reliable scalable secure applications in the cloud. 9780133858563 Hardcover 528 pages. How To Create A Continually Refreshed Amazon S3 Data Lake In Just One Day Aws Partner Network Apn Blog.
 Source: dribbble.com
Source: dribbble.com
Each pattern describes the problem that the pattern addresses considerations for applying the pattern and an example based on Microsoft Azure. If you wanted to do more than just business activity monitoring business reporting of these events you might want to look at Event Sourcing. Lets check tbl_test_audit_trail the audit log table the audit logs will be like. Inspirational designs illustrations and graphic elements from the worlds best designers. Audit Log Designs Themes Templates And Downloadable Graphic Elements On Dribbble.
 Source: success.outsystems.com
Source: success.outsystems.com
If you wanted to do more than just business activity monitoring business reporting of these events you might want to look at Event Sourcing. Two tables are required. These design patterns are useful for building reliable scalable secure applications in the cloud. Events funnel inputs into a single source. Monitor Usage With Audit Logs Outsystems.
 Source: pinterest.com
Source: pinterest.com
Audit logging after the action. Events funnel inputs into a single source. If you wanted to do more than just business activity monitoring business reporting of these events you might want to look at Event Sourcing. Inspirational designs illustrations and graphic elements from the worlds best designers. Data Tables Design Design Basics Data Data Table.
 Source: pinterest.com
Source: pinterest.com
TestIntegration contains integrated NUnit. Fowler provides an introduction here. Any IOC Dependency Injection framework to inject the abstract factory to. It is a Visual Studio 2017 solution with NET Core 22 projects. A Table With Row Grouping General Motors Corporation Citigroup Enterprise.
 Source: pinterest.com
Source: pinterest.com
These event objects are then processed to cause changes to the system and stored to provide an Audit Log. Using generic logging framework like Log4J to log the auditing information to desired format and data store. These event objects are then processed to cause changes to the system and stored to provide an Audit Log. Use a private browsing session not a regular session to access the Microsoft 365 compliance center because this will prevent the credential that you are currently logged on with from being used. Information Security Audit Checklist Template For Businesses 13 Samples Template Sumo Security Audit Checklist Template Checklist.
![]() Source: codeproject.com
Source: codeproject.com
The Admin Activity and Data Access audit logs are both exported in this format. The contents are represented as a protocol buffer and vary depending on the specific content being logged. Fowler provides an introduction here. Implement DB triggers to capture any change in data states and log in audit tables. Implementing Audit History Tracking Using The Prototype Pattern Codeproject.

Stores a basic set of historical changes with a record ID the blog post ID the change type NEW EDIT or DELETE and the datetime of that change. It should be dynamic enough to includes various types of audit log under an use case under discussion. So you might handle actual time history of a property with Temporal Property and use Audit Log to handle the. Theres an audit log thing that collects a bunch of audit record things. Implementing Audit Trail Using Entity Framework Part 2 Codeproject.
 Source: pinterest.com
Source: pinterest.com
In case of an exception the log entry might not be written so the audit log will not provide relevant contextual information for the exception. AuditID to serve as the identity ModifiedBy to serve. Each audit record is either an Edit or a Delete and contains the record that was changed and the old value of the object if applicable. Audit log entries should be written before an action - not after. Microservice Architecture Pattern Architektur Muster Sprache.
 Source: pinterest.com
Source: pinterest.com
In addition you might want to look at Audit Log as described by Martin Fowler here and perhaps more generally Temporal Patterns. Audit Log Builder Problem. It should be dynamic enough to includes various types of audit log under an use case under discussion. The Admin Activity and Data Access audit logs are both exported in this format. Azure Design Patterns Self Healing Transient Fault Handling Self Healing Pattern Design Design.
 Source: c-sharpcorner.com
Source: c-sharpcorner.com
The best design I can think of is two dates an external date of the event managed by the application using the DB and then an internal one of the record. The contents are represented as a protocol buffer and vary depending on the specific content being logged. For instance for the actual audit log topic with the enriched change events a time based retention policy might be suitable keeping each log event for as long as needed as per your requirements. Fowler provides an introduction here. Audit Trail And Data Versioning With C And Mvc.
 Source: dribbble.com
Source: dribbble.com
If you wanted to do more than just business activity monitoring business reporting of these events you might want to look at Event Sourcing. Figure 1 helps illustrate the point. Use a private browsing session not a regular session to access the Microsoft 365 compliance center because this will prevent the credential that you are currently logged on with from being used. For instance for the actual audit log topic with the enriched change events a time based retention policy might be suitable keeping each log event for as long as needed as per your requirements. Audit Log Designs Themes Templates And Downloadable Graphic Elements On Dribbble.







